

How to detect certain Spoofing/Phishing/Spearfishing e-mails.
Review any suspicious message to see who sent the message. Sometimes this is masked by Outlook or other client showing just the name and not the e-mail address. If you open the e-mail it should show you the originating address. Again, sometimes these are spoofed to look legitimate.
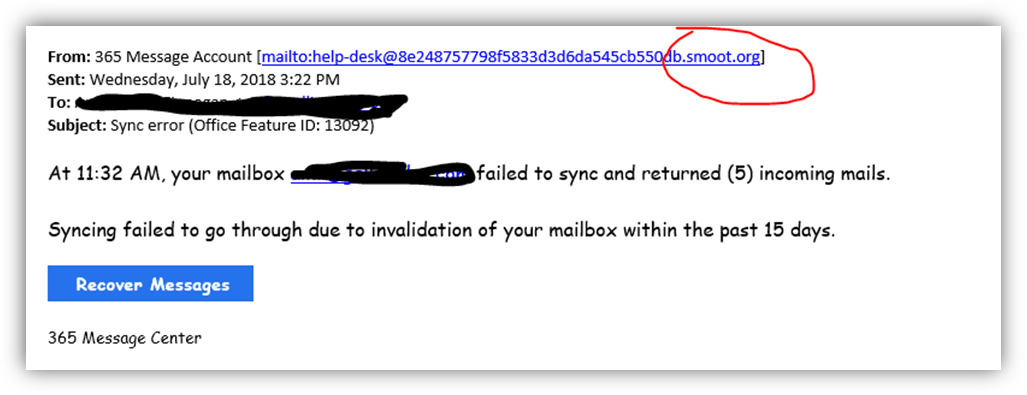
Below is a sample e-mail sent to one of our customers (I’ve blanked out her name), but you can see that the e-mail is coming from smoot.org – definitely not Microsoft.
Also look for bad grammar, mis-spellings and poor translation – “Syncing failed to go through” is a poor translation of “Your mailbox failed to synchronize”, and “due to invalidation” would be “due to invalid credentials”.
And, also when I hover over the link in the message, it is not taking me to any Microsoft site, but to a domain in New Zealand (.nz).
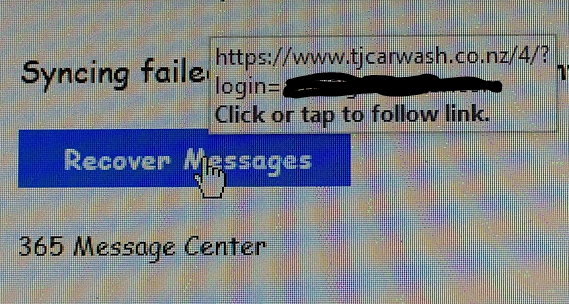
So, if we need to say it, DO NOT CLICK ON THE LINK, and then DO NOT ENTER YOUR PASSWORD.
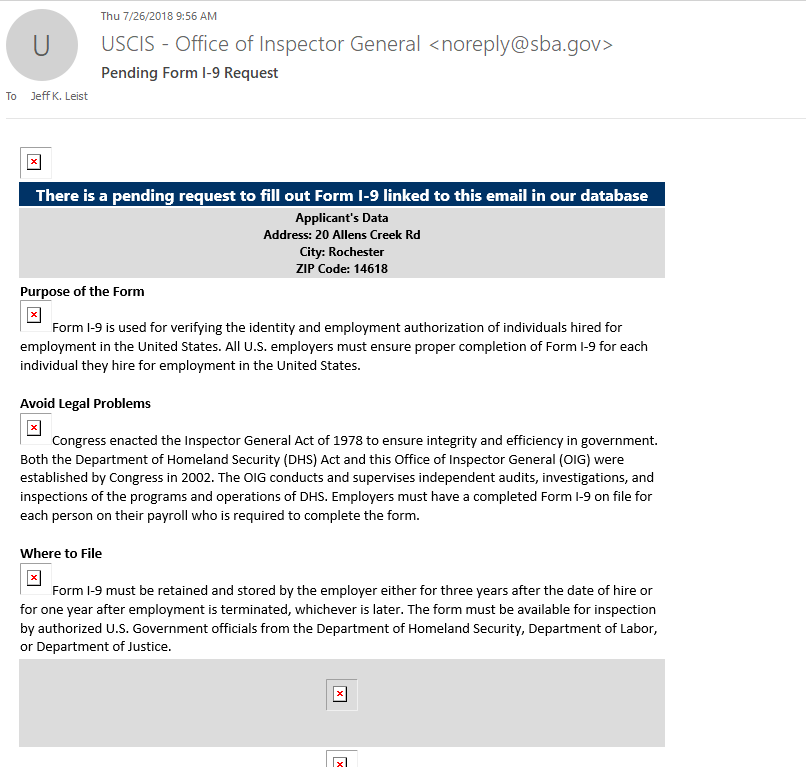
If you really want to investigate further, you can look at the Properties of the message, and review where it came from. This gets more difficult to read, but below is a message I received, and below it are the “Internet Headers” from the message. You get to these by opening the message and clicking on File, then Properties. In this case, the e-mail looks legitimate – the sent-from address looks OK, and there are no grammar or spelling issues that I see. On the other hand, the Inspector General of the Small Business Association (SBA) would not be requesting this information. And all the links and embedded images are being blocked.
So, I looked in to the Internet Headers – it shows that it originated in Japan, so definitely not the SBA.
Internet Header
Received: from EXCHANGE2K16.office.microworx.com (192.168.0.4) by
EXCHANGE2K16.office.microworx.com (192.168.0.4) with Microsoft SMTP Server
(version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256) id 15.1.1466.3
via Mailbox Transport; Thu, 26 Jul 2018 09:55:34 -0400
Received: from www1642.sakura.ne.jp ([219.94.192.52])
by smtp708.redcondor.net ({b3b1553c-8e73-11e7-bad5-5ba78457f1be})
via TCP (inbound) with ESMTPS id 20180726135548554_0708
for <jleist@microworx.com>;
Thu, 26 Jul 2018 09:55:48 -0400
X-RC-FROM: <noreply@sba.gov>
X-RC-RCPT: <jleist@microworx.com>
Received: from OOHASHI-SERVER (p655519.mie-ff01.ap.so-net.ne.jp [121.101.85.25])
(authenticated bits=0)
by www1642.sakura.ne.jp (8.15.2/8.15.2) with ESMTPSA id w6QDtdf9036758
(version=TLSv1 cipher=DHE-RSA-AES256-SHA bits=256 verify=NO)
for <jleist@microworx.com>; Thu, 26 Jul 2018 22:55:40 +0900 (JST)
(envelope-from noreply@sba.gov)
Message-ID: <201807261355.w6QDtdf9036758@www1642.sakura.ne.jp>
From: USCIS - Office of Inspector General <noreply@sba.gov>
About the Business
Have a question? Ask the experts!
Send your question

